Cloudfall Security Log Monitoring Service Subscription
Offering real-time collection and monitoring of security logs and events across your entire environment, providing effective detection and alerts for threats to your endpoints, networks, and data.
Common pain points
Lack of professional teams and expertise
The vast amount of data related to information security has posed numerous challenges for IT or security managers. Correspondingly, tasks such as receiving, caching, storing, and processing require professional teams and relevant expertise.
Consuming extensive time and resources
Managers expend considerable time attempting to extract useful information from recorded events and understand the root causes, requiring knowledge across domains including data, security, and systems. This process consumes significant time and resources.
Lack of experience and practice
The merging and correlation of events across different systems require extensive relevant experience and practice.
Security of the system itself
The security of the logging system itself has become an additional task for managers.
Flexible subscription model
Cloudfall’s own intellectual property tool portfolio and flexible and innovative subscription model can effectively help corporate customers solve the above pain points and focus resources and events on their core business. The
corresponding hardware, software and service subscription service packages can be configured according to different customer needs and scenarios, and users no longer need to spend time and energy to configure the infrastructure environment.
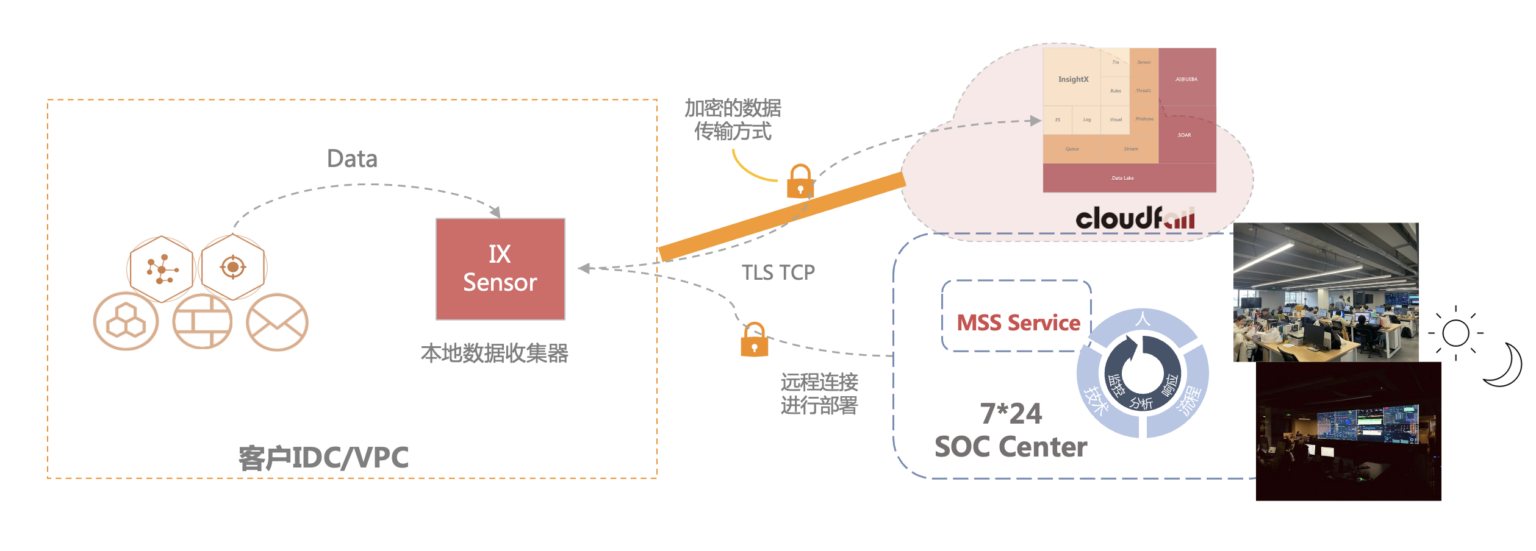
SaaS Model: IXCloud enables users to achieve rapid access and monitoring of security data through the local collector IXSensor.
Log collection
IXSensor
The Cloudfall Security Operations Platform, through the use of a local log collector called “IXSensor,” helps users with local event collection, enabling timely and accurate identification of security-related events. This ensures that you respond to valid threats effectively, apply the correct responses, and ensure that your critical assets are always adequately protected.
Differentiate between secure and insecure events.
With the aid of network firewalls, intrusion detection and prevention systems (IDS/IPS), VPNs, routers and switches, critical business systems, non-critical servers, and an abundance of endpoints generating extensive logs within an organization, it’s nearly impossible to discern the difference between security-related events and non-secure events.
Aggregation of security events
Our security operations platform collects security log and event information from all devices on the network, analyzing specific logs based on customer-identified use cases, policy violations, intruder behavior, and violation verification. This
comprehensive and technology-agnostic approach is a key factor in our ability to provide comprehensive network coverage and the best protection against the most sophisticated cyberattacks.
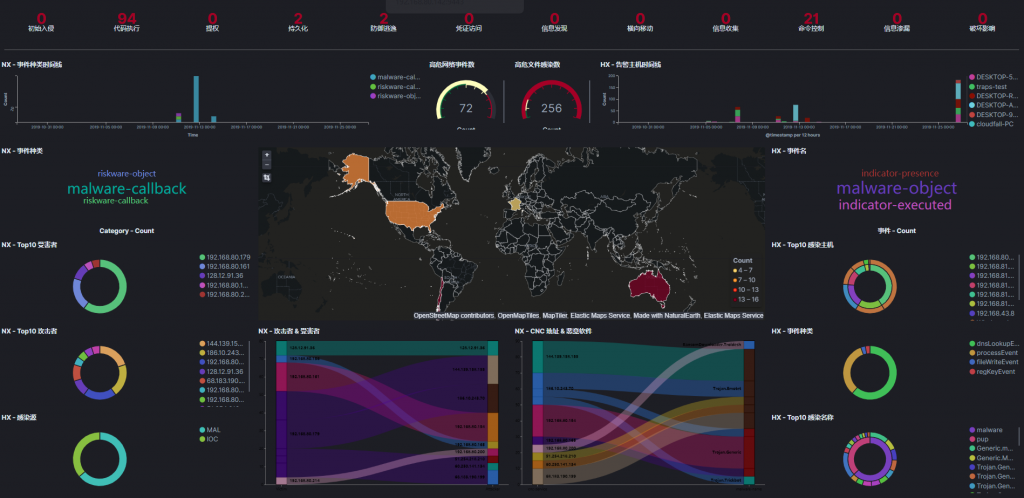
Cloudfall Security Operations Platform’s advanced proprietary log correlation engine allows us to detect the most sophisticated cyberattacks by analyzing and correlating raw system and security logs to identify trends over time. Cloudfall’s advanced log correlation engine combined with our highly skilled and professional security team will filter out all false positives, identify real security events and cyber threats that need to be addressed, and work with your team to eliminate them. Additionally, Cloufall can automatically detect use cases that customers are interested in.
Log retention
Log retention improves the ability to detect new anomalies that threaten the security of critical assets. Cloudfall’s log retention service makes it easy for you to comply with different regulations while reducing the hassle, cost and overhead associated with collecting, storing and reporting logs from hundreds of security and network devices, applications, database servers and other systems. Keeping logs securely does not need to consider the investment cost of hardware and software.
At the same time, we use cloud native technology to help users achieve cost-effective “hot”-“warm”-“cold” data tiering, and then minimize the cost of use under the premise of ensuring performance.





