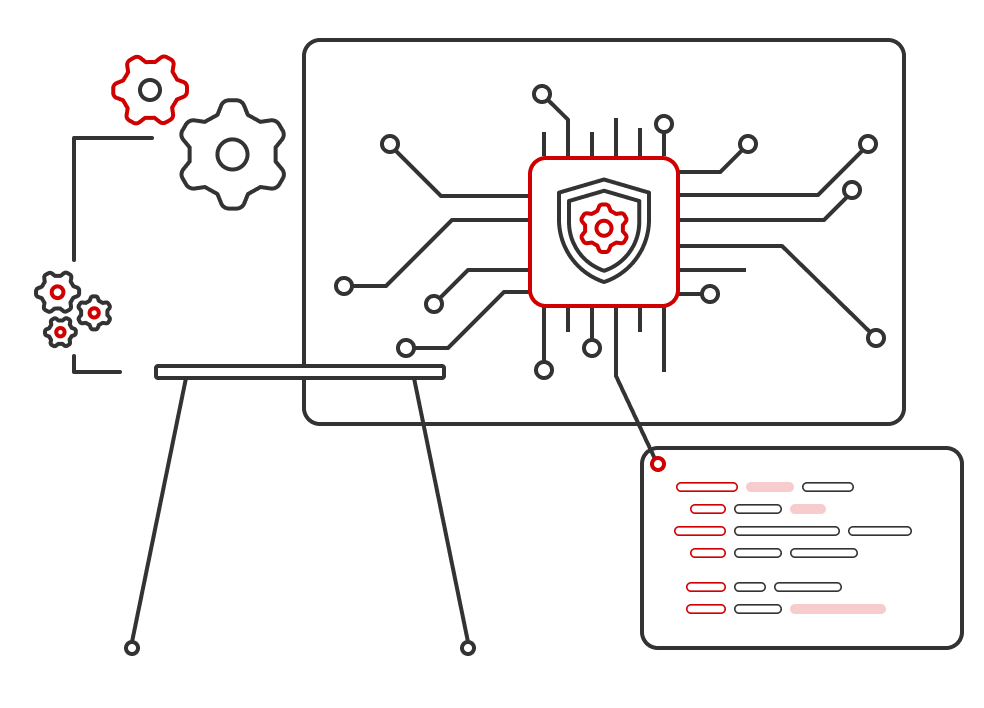
Powerful Intelligent Analytics Platform

AI-Powered Insights
Rule–Algorithm Synergy
Anomaly Detection Models
Intelligent Feature Extraction
Efficient & Flexible Deployment
Customized Services
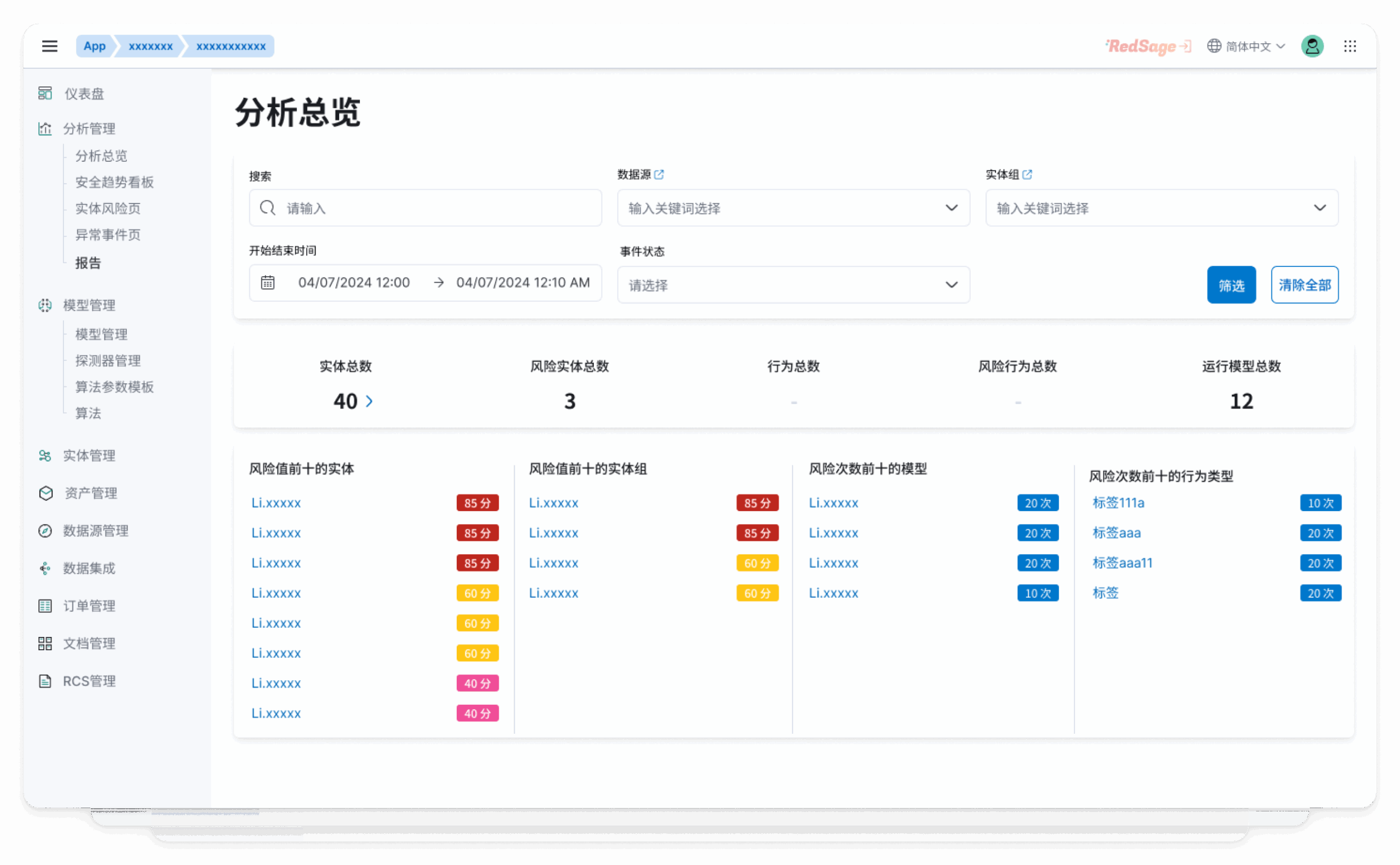
Comprehensive Risk Overview for Enterprise Security
Gain a holistic view of enterprise security through visualized analytics, enabling integrated risk monitoring, event tracking, and response management.
Global Visualization
Summarizes risk trends over time, clearly showing changes in overall security posture.
Rapid Traceability
Jump directly to any entity for detailed risk trends, behavior patterns, and anomaly insights.
Transparent Events
View key details including descriptions, detectors, and logs for clear traceability.
Operational Closed Loop
Respond directly within the platform for a seamless detection-to-resolution workflow.
Intelligent Analytics and Reporting – AI Empowering Security Operations
With RedSage conversational AI and AI Brief auto-reporting, the platform enables natural language analysis and automated report generation,
helping security teams efficiently summarize incidents, uncover insights, and respond to risks.
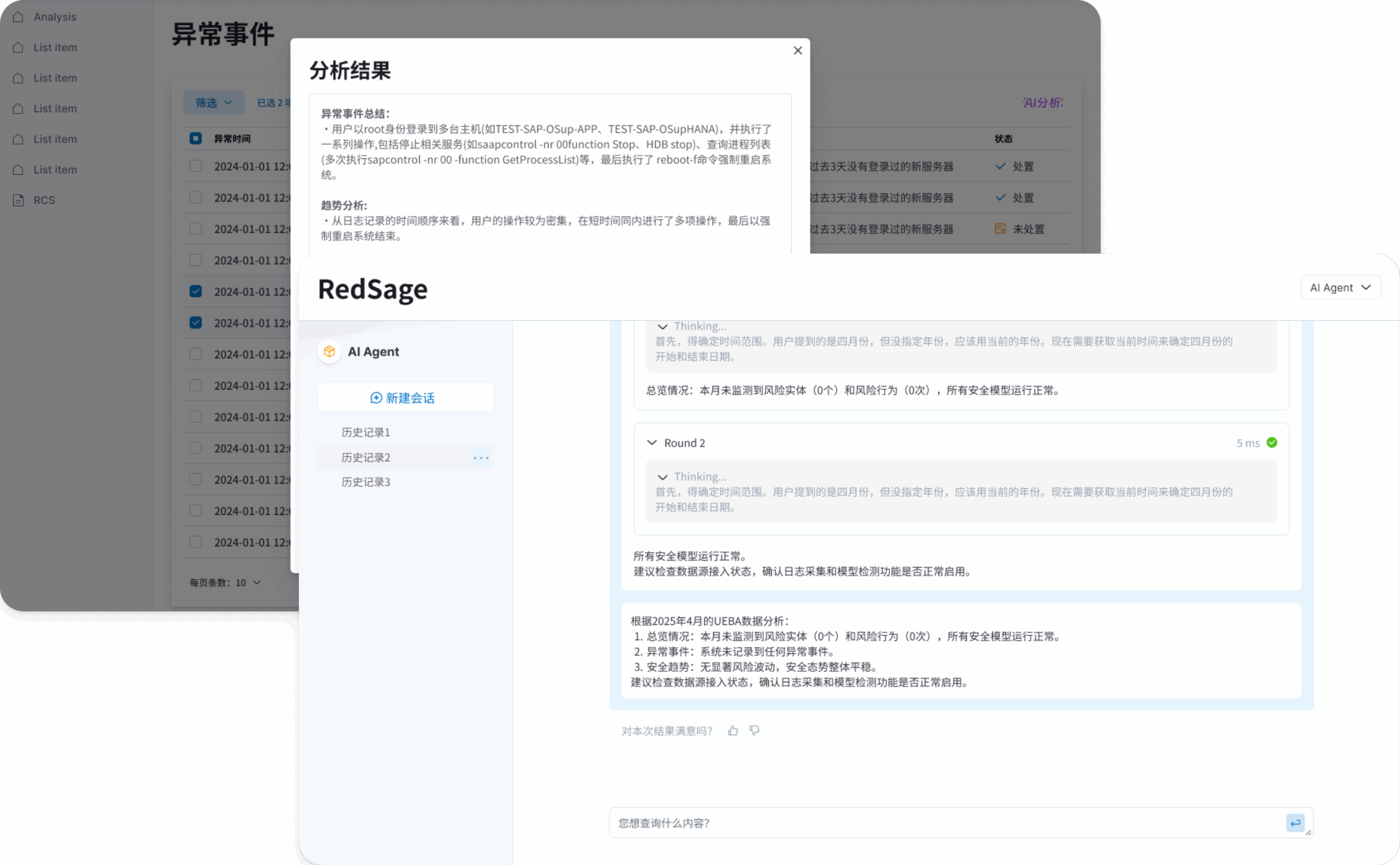
Conversational Analysis
RedSage supports complex data queries in natural language, making analytics intuitive and efficient.
AI-Assisted Decisions
AI interprets intent, analyzes trends, and delivers actionable insights for rapid, informed decisions.
Automated Reporting
AI Brief generates summaries, trends, causes, and solutions, streamlining the reporting process.
Multi-Model Fusion
Equipped with 14 models for diverse analytical and predictive scenarios, ensuring accuracy and flexibility.
Data Source Configuration – Easy Integration, Multi-Scenario Application
Data source configuration enables flexible data integration and processing,
supporting efficient behavior analysis and anomaly detection across diverse enterprise scenarios.

Multiple Data Sources
Connect logs, systems, network devices, and more for centralized management and analysis.
Offline + Online Prediction
Combine offline model training with real-time data for optimized predictive performance.

Multi-Scenario Output
Analysis results can feed security policies, alert management, reports, and other business systems.
API Support
Open APIs enable rapid integration with existing systems for data sharing and automation.
Use Cases
Intelligent Risk Detection
Identify anomalies and risks, generating alerts and reports to help enterprises detect issues and enhance protection.
Input Anomaly Monitoring
Monitor AI inputs and identify potential anomalies or malicious data through behavior pattern analysis.
Output Analysis
Analyze AI system outputs to detect abnormal behavior or deviations, uncovering potential risks or misuse.
Malicious Feature Detection
Identify malicious operations using feature and behavior analysis to support risk alerts and mitigation.
Behavior Anomaly Detection
Monitor AI system operations for abnormal patterns and detect potential threats using models and rules.
Deployment Options
SaaS
Leveraging public cloud and cloud-native tech for quick setup, lightweight, and on-demand subscription. Ideal for SMEs to gain fast security analysis and reduce costs.

On-Premise
Deploy locally or in private cloud for complete control over data, security, and compliance. Ideal for large enterprises or sensitive environments.