Agentic HROC
Combining AI technology with expert insights, continuously monitor and analyze user behavior to proactively detect risks, respond swiftly to incidents, and build an efficient security operations framework.
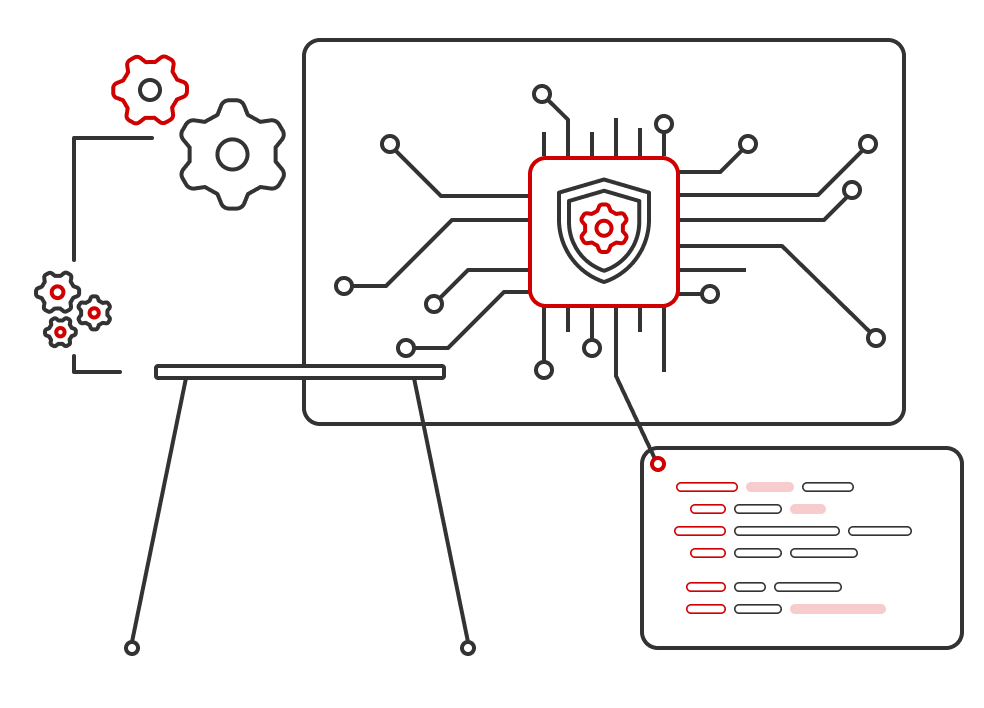
Risk Visibility: Real-Time Insight & Intelligent Protection
Unified behavior monitoring and intelligent analytics deliver immediate risk awareness and proactive control, ensuring internal threats stay visible and contained.

Monitoring
UEBA continuously detects anomalies and flags high-risk behaviors.

Response
Incidents follow a clear, end-to-end workflow for fast containment.
Optimization
Models and rules improve continuously for sharper detection.

Insights
Data-driven reports reveal trends and guide decisions.
Cloud-native and Agile Delivery, Flexible for Every Business Scenario
Powered by a modular, low-coupling design, InsightX delivers on-demand scalability and rapid alignment with dynamic business environments.
Built on DevSecOps and agile principles for continuous innovation.
Dynamic Risk Scoring
Real-time risk scores are generated for each employee, account, and action, based on multiple factors:
- Unusual login time, location, and device
- Frequency and volume of access to sensitive data
- Historical behavior deviations (compared with baseline behavior models)
- Employee status (e.g., resignation, role changes, performance)
Risk scores are updated in real-time, enabling enterprises to stay on top of high-risk behaviors and potential threats.
Tiered Alerts
Convert risk scores into tiered alerts for quick assessment and response:
- Low Risk (Monitor): Minor deviations from baseline, recorded and continuously monitored without disrupting normal operations.
- Medium Risk (Investigate): Clear anomalies requiring further investigation by the security or management team.
- High Risk (Urgent Action): Significant anomalies or sensitive actions triggering automatic interception or manual intervention.
Alert levels can be customized based on enterprise policies, ensuring precise warnings and reducing false positives and alert fatigue.
Automated Response
When an alert is triggered, predefined security actions are automatically executed:
- Account Lockdown: Temporarily suspend high-risk accounts to prevent potential violations.
- Permission Restriction: Dynamically tighten access permissions to prevent sensitive data leaks.
- Manual Review Trigger: Push high-risk events to security or management teams, creating tickets or initiating SOAR automation workflows.
Automated actions combined with manual review enable rapid response and controlled intervention.
Trend Analysis
Conduct multi-dimensional statistics and analysis on historical and real-time risk events:
- Summarize risk events by department, role, time period, and action type.
- Analyze patterns and trends of high-risk behaviors to identify potential risk hotspots.
- Provide decision-support data for management, such as optimizing access policies, adjusting monitoring priorities, or improving security training.
Visualize results (risk heatmaps, trend curves) to give enterprises clear insights into internal risks.
Protect Core Assets, Cover Key Scenarios
Start with a 12-month subscription, billed by risk scenario, allowing flexible cost control and shorter investment cycles.
Ex-Employee Data Theft
Accurately detect abnormal activities such as file access, downloads, and transfers after an employee resigns, effectively preventing core assets like technology and customer lists from being leaked.
- Abnormal Mass Download Detection
- Out-of-Hours Access Patterns
- Data Transfer Monitoring
- Sensitive File Access Patterns
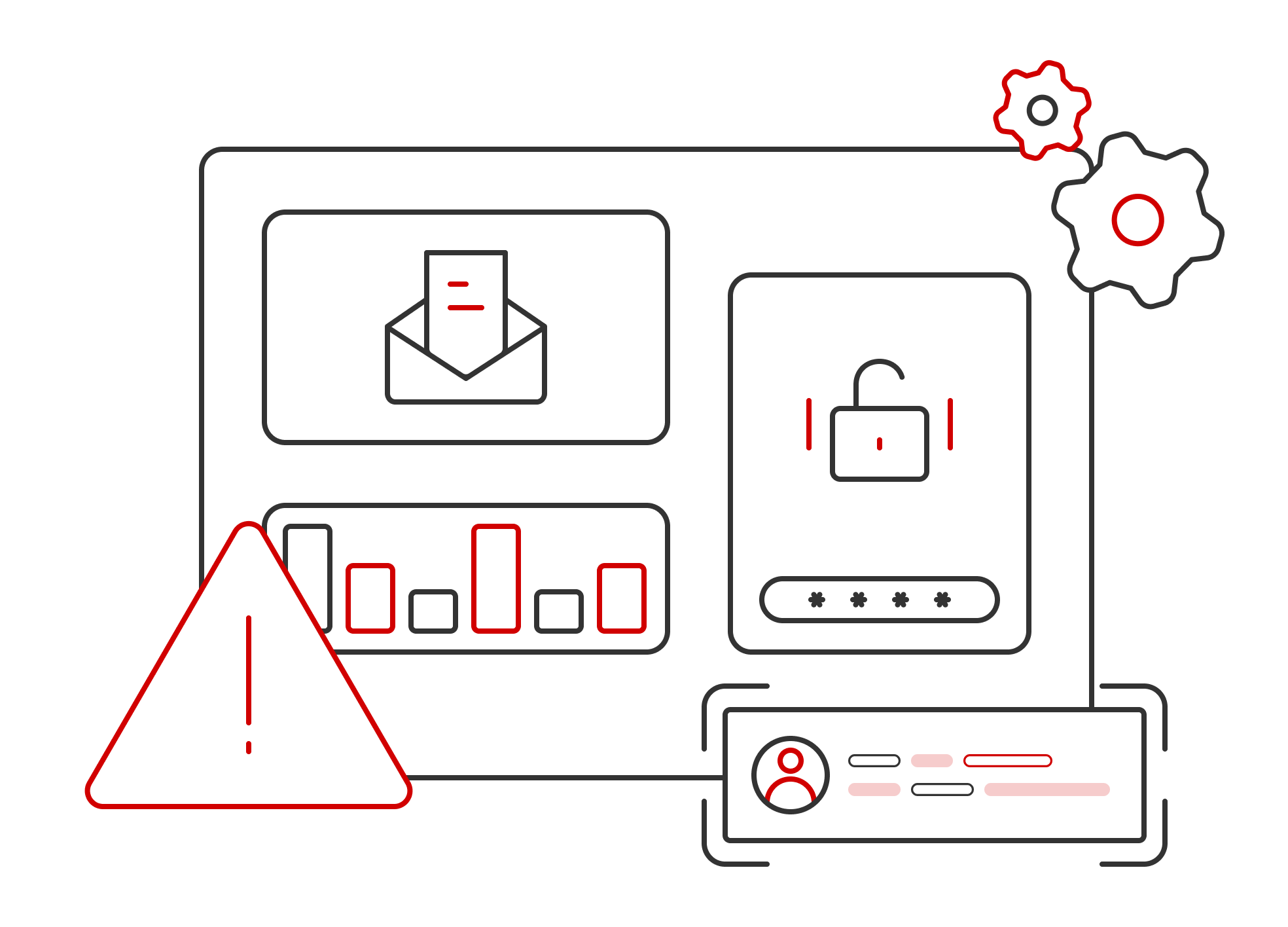
Flexible Scenario Expansion
Start with a 12-month subscription, billed by risk scenario, allowing flexible cost control and shorter investment cycles.

Insider Threat Detection

Cloud Detection & Response





